Technical Blogs - Our thoughts on what you may feel interested

Test Automation for IoT Devices V2.0
Imagine a world where IoT devices perform flawlessly, delivering consistent and reliable performance in every application, from smart homes to industrial automation. Achieving this level of excellence is now within reach, thanks to our groundbreaking Test Automation module. This innovative solution is set to revolutionize the way IoT devices are tested and validated, ensuring they meet the highest standards of quality and reliability.
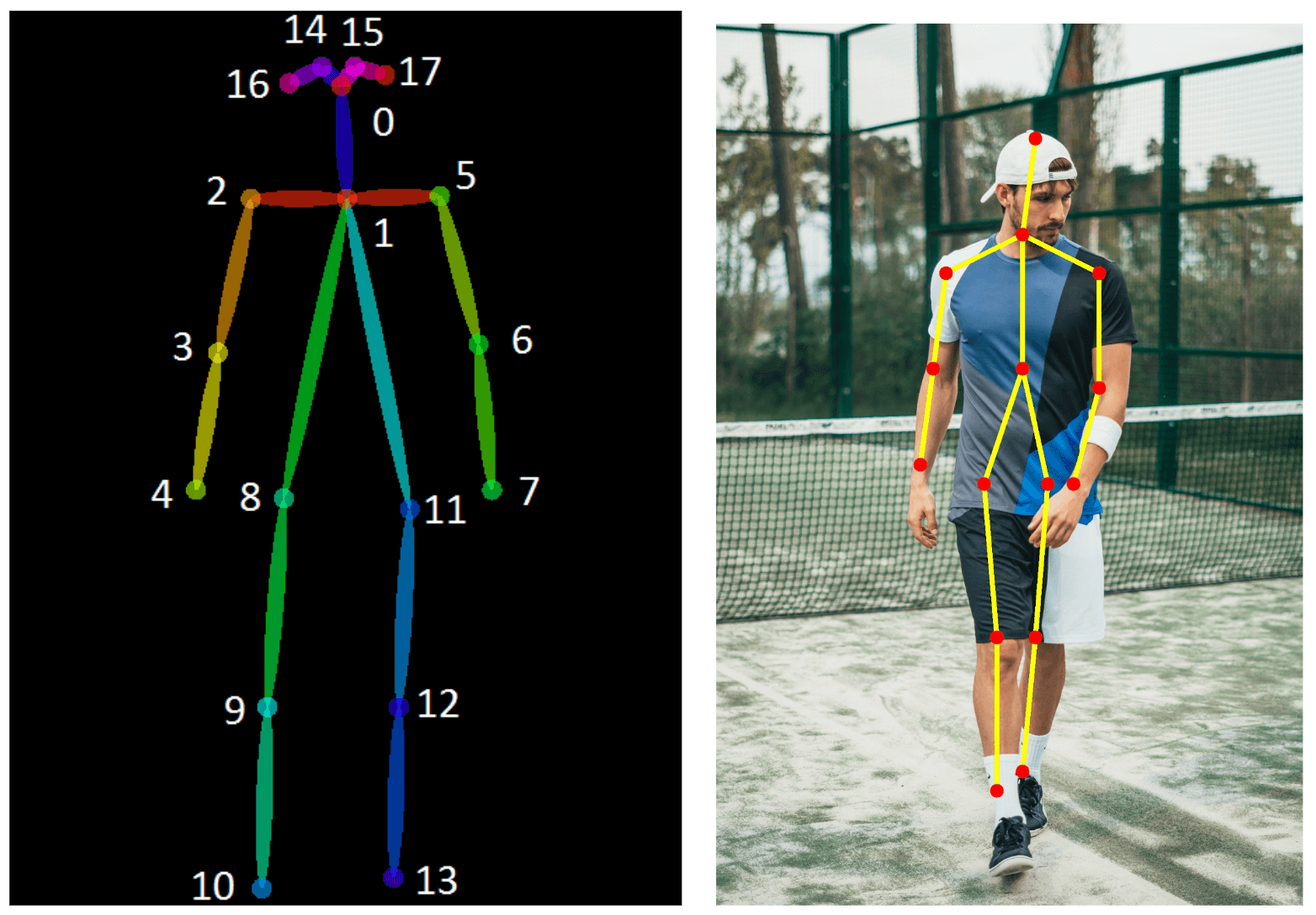
STEP-BY-STEP GUIDE TO BUILDING ANIMATED SKELETON VIDEO ON MOBILE APP
In today's AIoT ecosystem, ensuring privacy in real-time video-based computer vision applications while creating captivating user interfaces is crucial. This article will guide you through creating animated skeleton videos in a mobile application using React Native, focusing on enhancing user experience through smooth transitions and interactive elements.

POWER OPTIMIZATION IN BATTERY POWERED, MICROCONTROLLER AND IMU BASED MOTION PATTERN IDENTIFICATION DEVICES
Our requirement was to develop a device identification of specific vehicle motion patterns. Also it is needed to sync the data frequently with a mobile application (about once in a week) to get the data to the mobile application for further analysis. As the data is read once in a week. It is also needed to implement a saving ...

LoRa for Low Power Reefer Monitoring System
LoRa is the short term for Long Range and this technology is owned by the Semtech Corporation. LoRa is a modulation technique which is originated from Chirp Spread Spectrum (CSS) which is close to M-ary FSK modulation and it is operated in Sub- GHz of Sub- GHz range Radio Frequency, LoRa have uses like Long Range Communication and high penetration purposes like Reefer Monitoring Systems, Underground Data Monitoring Systems etc...
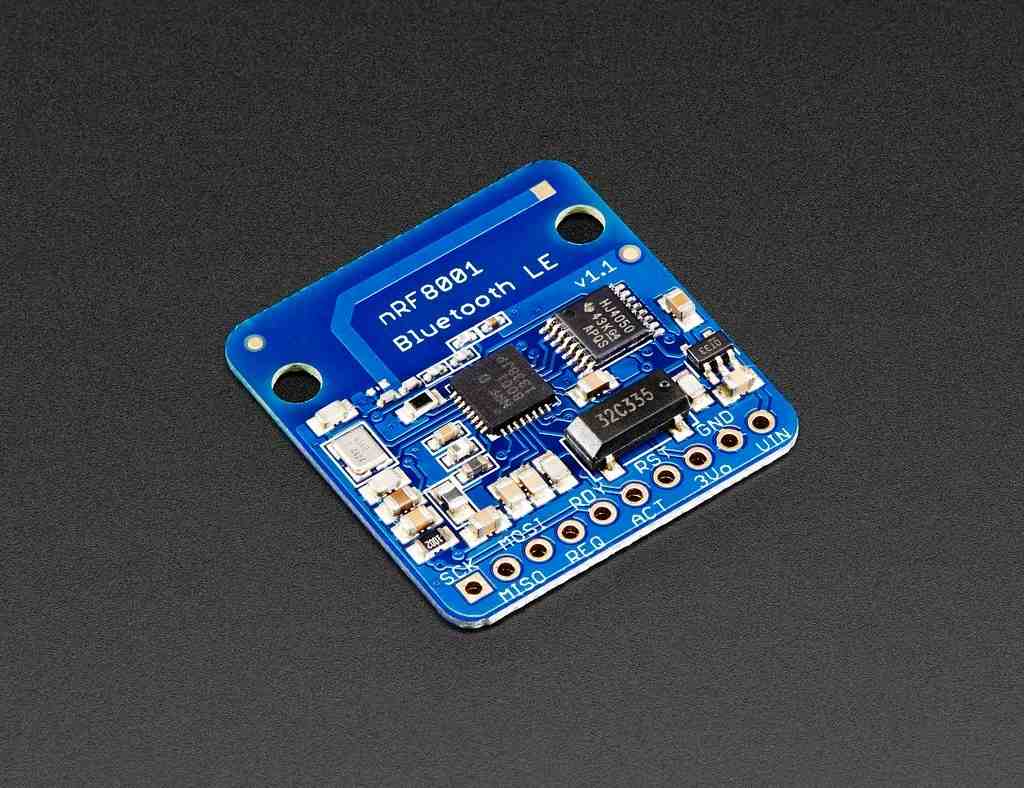
FIRMWARE UPGRADE OVER THE AIR USING BLE
Firmware upgrade during device lifetime is an essential requirement for most of applications to guarantee the performance and to keep the device updated with recent features with highest security level. Updating the firmware can be done using physical links such as USB, UART or I2C but it requires a physical connection. It is possible to update the device firmware in real time using wireless connection which is called...

INDOOR FORKLIFT LOCALIZATION USING BLUETOOTH LOW ENERGY BEACONS
Nowadays we can see a lot of applications on object localization. Depending on the applications developers use different technologies to implement localization. Indoor and Outdoor are the two major categories which determines the technologies we can use. The problem of localization has largely been solved for outdoor situations...
Cryptography and how itis used to secure today’s WIFI networks
Hi all, Hope this article will be beneficial and that you learn something from this. Through this article, I will describe what is cryptographyand its different use cases. This will be vital in order to understand how we use these techniques in a wireless network. So let’s begin. I am sure many of you have come across the term cryptography. In the beginning, it may sound a bit intimidating. But once you get to know what...

HOW CRYPTOGRAPHY IS USED IN A WIRELESS NETWORK TO SECURE IT.
In this article, I will be sharing how wireless security is achieved specifically targeting IEEE 802.11 standard which is simply known as WIFI. I assume that you have some knowledge about WIFI, so I won’t dig deep into WIFI standards. But something which is good to know is that WIFI6 is rolling out and is already supported by some newest flagship electronic devices. While 802.11g/n uses the 2.4GHz ISM band, 802.11ac uses...

WIDEN YOUR PURVIEW ON THE EFFICACY OF YOUR PRODUCT!
A core ideology of a product is usually planned in many stages before the actual production. It is customary to produce several prototype versions including the successful features from the previous stages and new changes which are often being tested for usability at the current stage. After completing the production stages, the usual practice comprises branding and installation. At this point, the product is proven to...

Auto Checking the Latest Version of a Mobile App Version from the Playstore
When the user opens the mobile app, the app should fetch the latest version in the play store and compare the current app version and alert the user to update the app if the current version is behind the newest version. The initial approach was to use the react-native-version-check library. But after a few weeks of implementing it....

Data communication under the soil using Lora technology
In agriculture, IoT is primarily used for field parameter monitoring and automation, with the goal of assisting farmers in increasing crop productivity

Architecture for ensuring Privacy in Real Time Video based Computer vision applications
A privacy policy is a legal document that outlines how a software product or service collects, uses, stores, and shares user data. It serves as a transparent communication tool between the software provider and its users regarding the handling of their personal information. Most of the time users agree to privacy policy without reading or properly understanding its content.