You are in the second part of the series, how cryptography is used in a wireless network to secure it.
Briefly about WIFI
In this article, We will be sharing how wireless security is achieved specifically targeting IEEE 802.11 standard which is simply known as WIFI. We assume that you have some knowledge about WIFI, so We won’t dig deep into WIFI standards. But something which is good to know is that WIFI6 is rolling out and is already supported by some newest flagship electronic devices. While 802.11g/n uses the 2.4GHz ISM band, 802.11ac uses the 5GHz spectrum and now WIFI6 (802.11ax) will be using the 6GHz spectrum. While the data rate is increasing and networks shifting into less congest frequency bands, due to the decrease in wavelengths the range has been reduced as of low signal penetration through solid objects. Sacrifice something to gain something else. So that’s a simple introduction to WIFI. Now let’s move onto WIFI security standards.

As a user, we have used different ways to connect to a wireless network. But as long as we were able to connect to the internet through an access point we were satisfied. But knowing what is really happening behind the scene is simply fascinating. In some places, there were open networks. We just connected to it without configuring anything. Then we have our personal routers for which we enter a password (preshared key) to connect. Anyone who knows the password can connect to it. Then there is another way to connect to WIFI in our universities. In universities, we have our username and password. Our unique credentials. Someone who is from the outside cannot connect to the network even if it is visible. The only possible way is, asking for credentials from a student and connect to the Eduroam network pretending to be that student. We guess that rarely happens. And then there is another far superior form of security which uses certificates to authenticate users/machines to access points and it is widely accepted as the golden security standard. You don’t have to enter anything to connect. In another way, with minimal user interaction, you can connect to a network with the greatest security. Without any doubt when it comes to the deployment of such systems it is much difficult compared to the rest. So as you can see there are various security standards that are in effect. We will introduce them briefly below while focusing more on current security standards.
WIFI Security Standards
Introduction
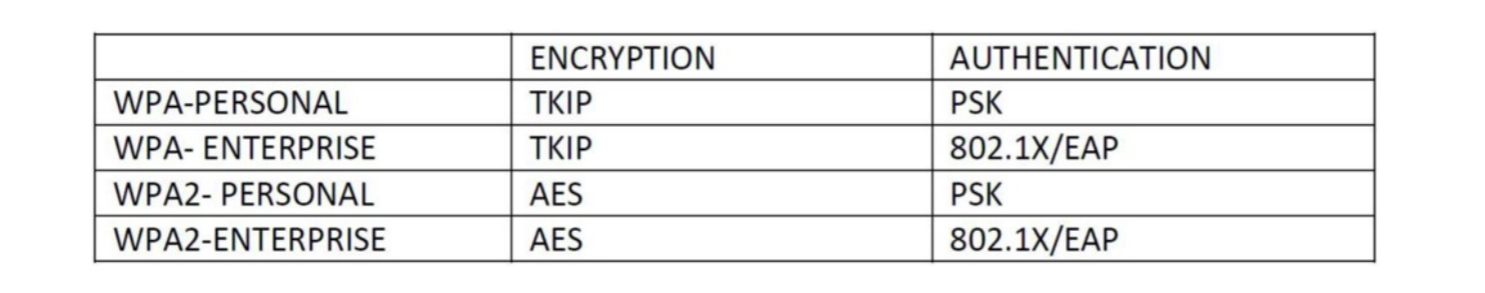
So the first security standard was called Wired Equivalent Privacy(WEP). Since many vulnerabilities had raised and thus proven to be insecure, it is no longer in use. Due to these vulnerabilities WIFI alliance directly came up with a replacement called Wireless protected access (WPA). There are two standards under WPA namely personal and enterprise. Again, due to some security breaches in its encryption standard, an updated version of the standard named WPA2rolled out. A significant difference between these two was the use of encryption algorithms. WPA2 uses AES with CCMP (Cipher Block Chaining Message Authentication Code Protocol). WPA3 was recently rolled out but there are, no major differences compared to widely adapted WPA2. Due to WPA2 still being secure, enterprises are not in hurry to accept the new update. One such change in WPA3 is, addressing the brute force attack on improperly configured old WPA2 personal networks.
We will mainly focus on WPA2 standards as it is what we use mostly in our day-day activities. Below is a table of comparison of standards used in the encryption and authentication process.
We explained what the AES algorithm is and the type and features in my previous article. What We didn’t explain is CCMP. Long note short CCMP is a way of applying the AES encryption to our text which makes it more secure. This makes things even more difficult for hackers to decrypt our messages. Since TKIP was vulnerable and many attacks were encountered in the past, communities soon adapted to the new WPA2 standard. symmetric encryption is used for general data communication between two entities as it is much faster. In enterprise modes, asymmetric encryption is used for authentication purposes. After a successful authentication process, a session key is generated at both ends for a secure encrypted tunnel for communication.
WPA/WPA2 Personal
In our home routers, we use WPA/WPA2 personal mode which is commonly known as WPA/WPA2-PSK. A pre-shared key(PSK) is also called a Wi-Fi Security Key, a WEP Key, or a WPA/WPA2 Passphrase. Using this PSK a 256bit long pairwise master key is generated for encryption/decryption. In personal mode, the security of the network depends on the trust kept by people who use the network. When more and more people connect to the network higher the risk of one of them leaking the password. So for enterprises or similar kinds of larger networks whose biggest concern is security, PSK is not the ideal solution. Therefore, they have to move on to a much secure enterprise mode. Things get more interesting and fascinating when moving on to enterprise mode. We will cover briefly them in this article.
WPA2-Enterprise
This is the golden standard for wireless network security. Deploying WPA2-Enterprise requires a RADIUS server, which handles the task of authenticating network users as an enterprise router could not handle the authentication process. The actual authentication process is based on the 802.1x policy and comes in several different systems under the EAP framework which We will explain in a moment. Because each device is authenticated before it connects, a personal, encrypted tunnel is effectively created between the device and the network. While the security is largely increased, the difficulty of deployment is also increased. Thus, the tradeoff.
In order to deploy such a system, some key components are needed.
1. Client/supplicant
User or the machine which needs to be authenticated to securely connect to the wireless network.
2. Access point
Enterprise routers/wireless controller. Usual home routers don’t support enterprise mode.
3. Radius server/Authenticator
This will handle the authentication process. After confirming the credentials/validating the client certificate through the help of an active directory/identity store, clients will be granted access to enter the network securely.
Want to know more about radius server. Visit herehttps://freeradius.org/
WPA2-Enterprise Authentication
There is a relationship between authentication and encryption in the 802.1x standard. encryption keys are derived after a successful authentication process. Different authentication methods are defined under the Extensible authentication protocol (EAP). EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions for authentication methods called EAP methods. Below listed two common EAP methods.
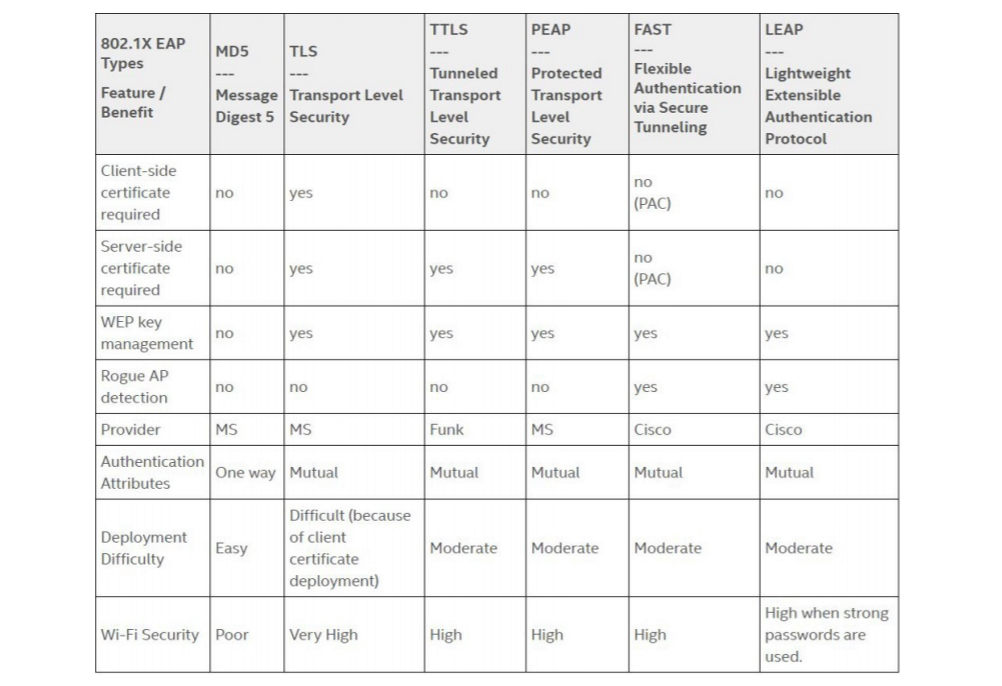
1. Credential based authentication
PEAP-MSCHAPv2 is the most common credential-based authentication protocol in use. Almost all the Eduroam networks and many enterprises use a username/password to authenticate users. Compared to certificates, it is relatively easy to deploy but these networks are still susceptible to many problems like brute force attacks, over-the-air attacks, etc.
2. Certificate-based authentication
This is the strongest WPA2-Enterprise standard. it relies on the asymmetrical cryptography of digital certificates for authentication. These certificates need to be installed on devices initially but once it is done, users don’t need to enter any passwords or credentials to access the network. Once the device is in the range of the network, it simply gets connected. Thus, the best user experience.
EAP-TLS is widely considered the most secure EAP standards as of today mainly due to the requirement of client-side certificate and validation of server certificate.
That’s it for now. We hope you enjoyed reading. Thanks for reading it till the end and We hope that you learned something out of this.